This is why its also known as public key encryption public key cryptography and asymmetric key encryption. Symmetric encryption is the oldest and most-known encryption technique.

What Is Asymmetric Encryption How Does It Work Infosec Insights
Asymmetric encryption is used to initiate the conversation among the users which involves exchanging secret keys for symmetric encryption.

. Common examples include SSLTLS connections and messaging applications such as Signal Whatsapp that use end-to-end encryption to prevent third-parties. One referred to as the Public Key and the other referred to as the Private Key. Symmetric-key encryption uses the same cryptographic keys for both the encryption of the message by the sender and the decryption of the ciphertext by the receiver.
First of all they exchange their public keys. Anyone can see this and access it. Symmetric key encryption relies on mathematical functions to encrypt and decrypt messages.
Only the authenticated recipient has access to it. Correct answer to the question Describe how asymmetric encryption is used to send a message from User A to User B that assures data confidentiality authentication and integrity. After the communication is established and a secret key is exchanged symmetric encryption is used for the whole duration of the communication.
This is part of a process known as the TLS handshake of which there are. Public Key is One of the keys in the pair that can be shared with everyone whereas Private key is the other key in the. When the message is encrypted with the public key only the corresponding private key can decrypt it.
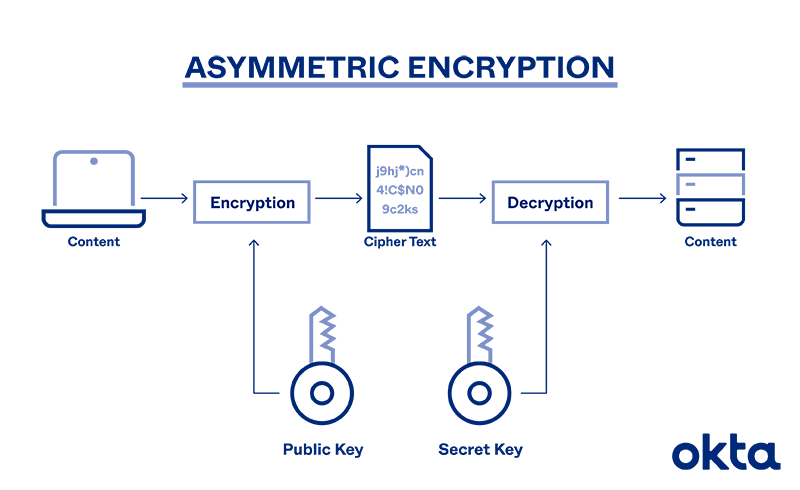
Why do you need two keys. Asymmetric encryption is a type of encryption that uses two separates yet mathematically related keys to encrypt and decrypt data. Now User 1 can share his sensitive document again by taking the document and encrypting it with User 2s public key.
Asymmetric encryption uses two keys to encrypt a plain text. Be specific as to the keys used and how they achieve the three goals. This key pair is mathematically related to each other with algorithms and is called the Public Key and the Private Key.
These two keys are separate but equal and theyre both required to decode a message. TCO C Describe how asymmetric encryption is used to send a message from User A to User B that assures data confidentiality authentication and integrity. The public key is open to everyone.
A Definition and Explanation. Decrypt a message from a friend. Two keys are used in asymmetric cipher eg RSAa public and a private one.
This is the process of asymmetric encryption. Definition of Asymmetric Encryption. A key is a.
Asymmetric encryption is a type of data cipher also called a public-key cipher where the cipher key also known as the common key and one the other side decode key also known as the personal key vary. The message is now saved in a new file called messagetxtasc which is encrypted and addressed to your recipient using his or her public key. User 1 gives his public key to User 2 and User 2 gives his public key to User 1.
The keys are simply large numbers that are paired together. A private one and a public one. Alice wants to send a message to Bob.
As stated above Asymmetric Encryption or Public-key Cryptography as you name it uses a pair of keys for encrypting and decrypting messages. Weve also established that what one key encrypts only the other can decrypt. This ensures the security of asymmetric cryptography making sure only the intended recipient can perform decryption.
Describe with the help of a graphical representation how they can achieve both confidentiality and authentication using asymmetric encryption. Describe with the help of a graphical. Bob generates two keys a public key known the the world and a private key only known to Bob.
Asymmetric encryption often called public key encryption allows Alice to send Bob an encrypted message without a shared secret key. Asymmetric encryption is used for keys exchange used for symmetric encryption. Both decide to use asymmetric encryption to ensure confidentiality and authentication for their communication.
Only with the matching personal key will a message encode with the common key be decoded. Asymmetric cryptography also uses mathematical permutations to encrypt a plain text message but it uses two different permutations still known as keys to encrypt and decrypt messages. The keys in practice represent a shared secret between two or more parties.
Lets now take a look at how Users 1 and 2 can use asymmetric encryption to exchange messages securely. All you have to do now is send an email to the recipient and attach the encrypted file to it. Symmetric encryption is asymmetric.
The public one is available for everyone but the private one is known only by the owner. Weve established how Asymmetric encryption makes use of two mathematically linked keys. Asymmetric encryption is quite the opposite to the symmetric encryption as it uses not one key but a pair of keys.
Secret keys are exchanged over the Internet or a large network. Alice sends Bob a message and Encrypts it with the Public Key that is known the world. You use one to encrypt your data which is called public key and the other to decrypt the encrypted message which is called the private key.
Be specific as to the keys used and how they achieve the three goals. It is important to note that anyone with a secret key can decrypt the message and this is why asymmetric encryption uses two related keys to boosting security. The public key encrypts data while its corresponding private key decrypts it.
It ensures that malicious persons do not misuse the keys. The way that HTTPS works is that we use asymmetric encryption to first authenticate the website server and to exchange symmetric session keys. In comparison asymmetric key encryption also called public key cryptography uses two separate keys to encrypt and decrypt messages.
If you have only one decryption is impossible. Figure 15-1 provides an overview of this asymmetric encryption which works as follows. Security in an asymmetric encryption environment comes from two keys.
Bob receives the message and decrypts it with his Private Key which is only known by him. Describe how asymmetric encryption is used to send a message from User A to User B that assures data confidentiality authentication and integrity. There is a secret key but only Bob knows what it is and he does not share it with anyone including Alice.
The encryption is called symmetric because it uses a single key for both encryption and decryption. Asymmetric cryptography which can also be called public-key cryptography uses private and public keys to encrypt and decrypt the data. However they are asymmetric means not identical.
With asymmetric cryptography a public key that can be shared with anyone gets used to encrypt messages while a private key thats known only by the recipient gets used to decrypt.

Si110 Asymmetric Public Key Cryptography
15 1 Asymmetric Encryption Explained Chapter 15 Asymmetric Encryption Part Iii Net Cryptography Net Programming Security Programming Etutorials Org
15 1 Asymmetric Encryption Explained Chapter 15 Asymmetric Encryption Part Iii Net Cryptography Net Programming Security Programming Etutorials Org
0 Comments